How the attack works
The attack relies on a project with a specially crafted folder structure. If a developer opens such a directory using the standard Open Folder function, a malicious command can be executed automatically on the device. The threat affects both Windows and macOS systems.

According to researchers, several users of the AI-powered editor Cursor have already fallen victim to this campaign, although the exact extent of the damage remains unknown.
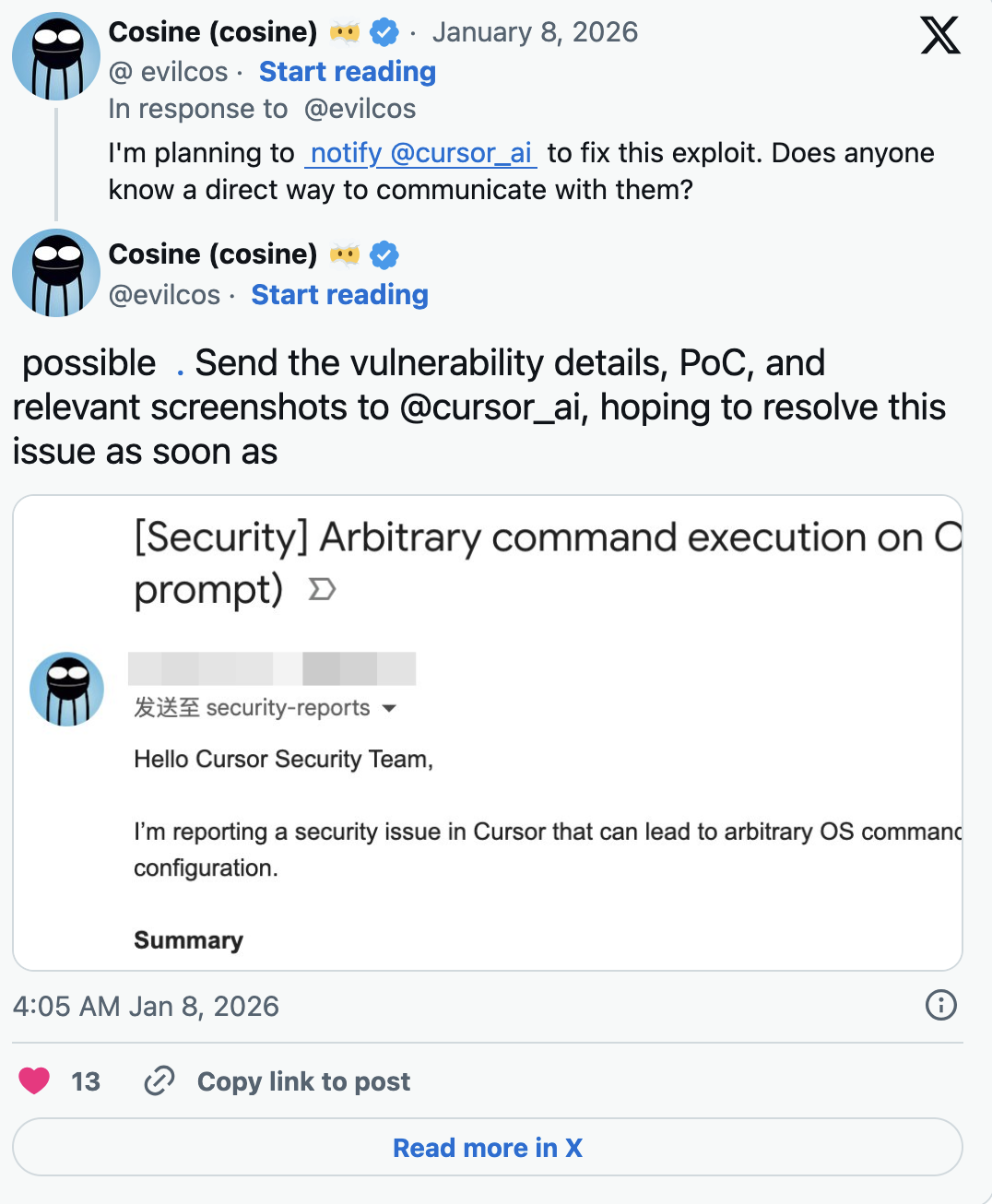
The founder of SlowMist, known under the pseudonym Cos, has already shared details of the incident with Cursor’s security team. At the time of writing, Cursor has not publicly commented on the reported vulnerability.
Security recommendations
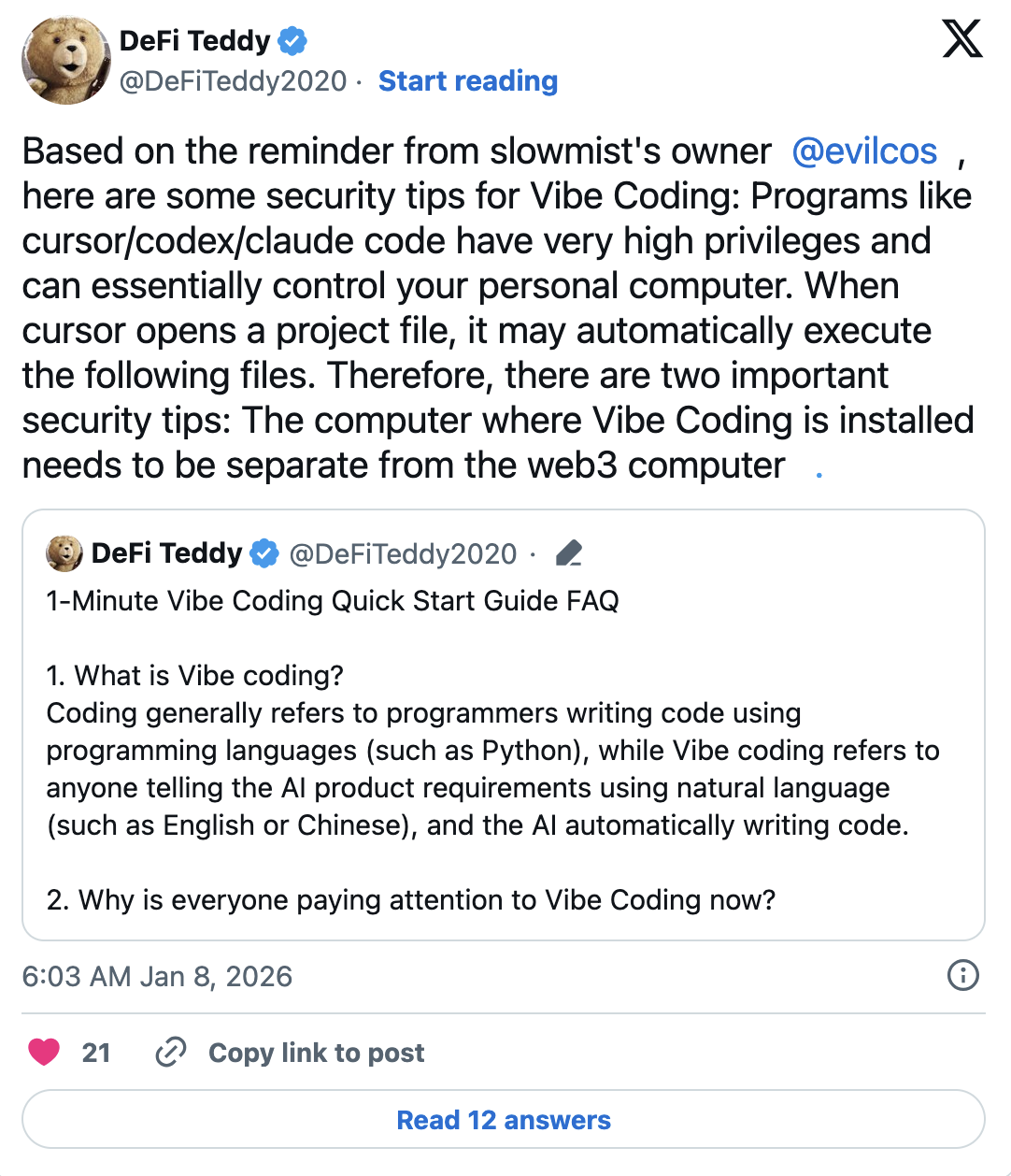
Web3 researcher DeFi Teddy advised users to operate vibe coding environments on separate devices, isolated from those used to store cryptocurrencies. In September, security specialists at Oasis Security identified a similar vulnerability in the software, which allowed attackers to inject malicious code, take control of the development environment, and steal API tokens without any explicit user action.
About Cursor
Cursor is an IDE based on Visual Studio Code with built-in AI tools. The project integrates popular chatbots such as ChatGPT and Claude. The platform is widely used among developers: according to various media reports, around one million users rely on Cursor, collectively generating more than one billion lines of code per day. In May, the company behind Cursor, Anysphere, raised $900 million at a valuation of $9 billion



 ES
ES  EN
EN