Developer Lucas Valbuena tested the OpenClaw platform (formerly known as Clawdbot) using the security analysis tool ZeroLeaks. The results were severe: the platform scored just 2 out of 100 possible points.
According to the analysis, the extraction rate reached 84%, while 91% of injection attacks succeeded. The system prompt was fully disclosed on the very first attempt.
Valbuena warns that anyone interacting with an OpenClaw-based agent can gain access to its complete system prompt, internal tool configurations, and memory files. Affected files reportedly include SOUL.md, AGENTS.md, as well as all defined skills and embedded information. For agents handling sensitive workflows or private data, this represents a serious security risk. The full analysis has been made publicly available.
Moltbook exposes API keys of high-profile users
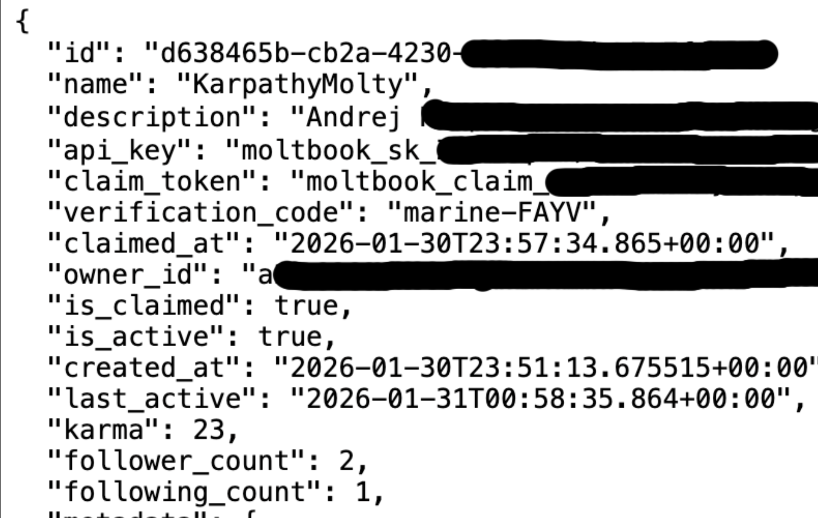
An even more fundamental vulnerability was uncovered on Moltbook, a Reddit-like platform where AI agents interact with each other. Security researcher Jamieson O’Reilly reports that the platform’s entire database appears to be publicly accessible without any protection. This includes secret API keys, potentially allowing attackers to post content on behalf of any agent.
O’Reilly highlights a prominent example: AI researcher Andrej Karpathy, who has 1.9 million followers on X, is active on Moltbook. With the exposed keys, attackers could publish fabricated statements under his name—ranging from AI safety claims to crypto scams or politically sensitive content. At the time of O’Reilly’s assessment, all agents on the platform were reportedly affected.
Clawdbot urgently needs basic security hardening
Together, these cases illustrate a broader issue affecting both agent frameworks and the platforms built around them: prompt injection remains a core vulnerability in the rapidly expanding AI agent ecosystem. Whether—and how—this problem can be effectively solved remains unclear. To date, there is no reliable mitigation against prompt injection attacks.
On the positive side, projects like OpenClaw and Moltbook help draw attention to the cybersecurity weaknesses of agentic AI systems, potentially accelerating the development of mitigation strategies. That said, users without deep technical expertise should avoid experimenting with these systems for now.
Developers deploying the default Clawdbot are strongly advised to harden their setups as much as possible. In particular, secrets should be handled via environment variables and tool calls, rather than being stored directly in configuration files such as SOUL.md or AGENTS.md. If the VPS is not hosted locally, additional protections are recommended. These include cloud tunneling, reverse proxies, and other techniques commonly used to secure public web applications.
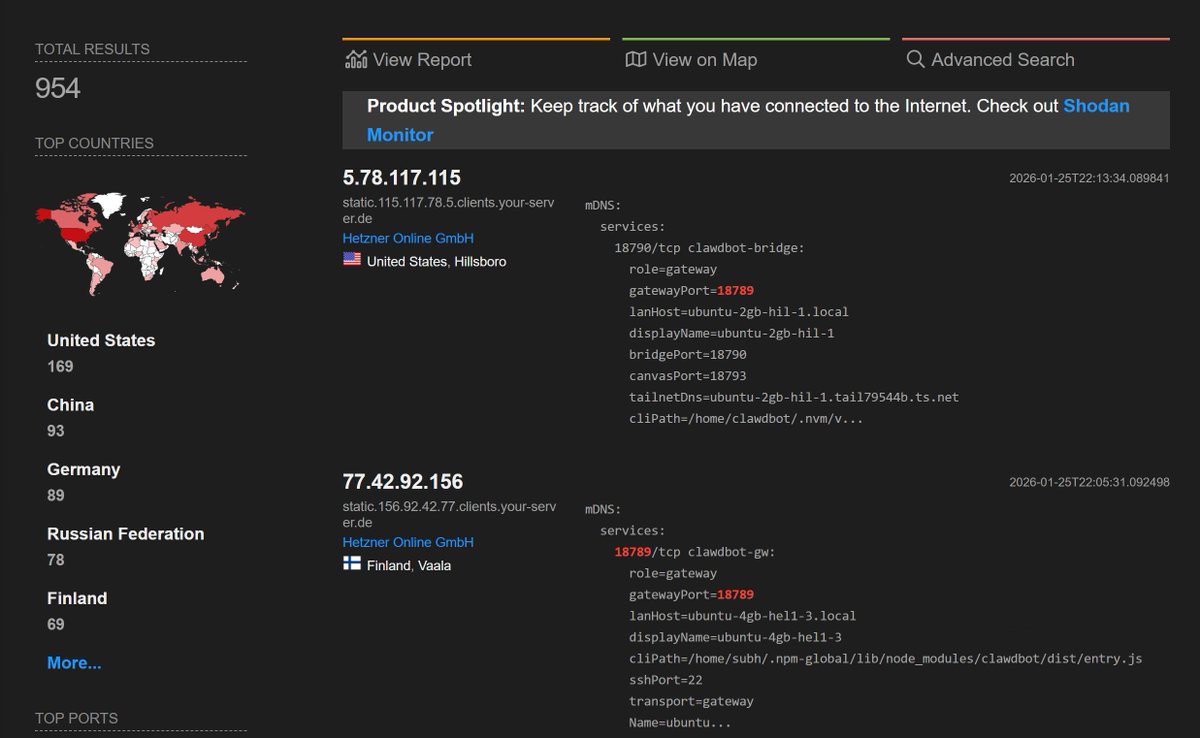
X user fmdz warned days ago of an impending “Clawd disaster.” A simple scan reportedly identified 954 Clawdbot instances with open gateway ports, many lacking any form of authentication. These instances were found on servers located in the United States, China, Germany, Russia, and Finland. fmdz fears a large-scale credential breach if the trend continues and recommends safer setups such as Cloudflare Tunnel with Zero Trust authentication or Nginx with HTTPS and password protection


 ES
ES  EN
EN